Most businesses are worried about the safety of their computer systems. They are scared that someone may get into their system and steal their sensitive and important data. This is called a data breach or a cyberattack. IT audits help to check if your business is safe from these attacks.
An IT audit looks at how well your business protects its computer systems. But you must be thinking, what are the IT audit controls checklist? And how can your business have them? Don’t worry, in this article, we will explain IT audit controls clearly. We will tell you what they are and why they are so important for your business.
We will also talk about what are IT audit controls checklists, and answer common questions about IT audit controls that almost every business has. At the end, we will tell how TMI can help you do a full IT audit. So, let’s get started.
What Are IT Audit Controls?
To understand IT audit controls, think of your computer systems as a strong phone password. The data inside is very valuable to you. IT audit controls are like the security measures put in place to protect this password. These include rules, steps, and technical tools. They are made to achieve certain safety goals. These goals can be:
- Confidentiality: Making sure only approved people can see sensitive information.
- Integrity: Keeping data safe from any unauthorized changes or damage.
- Availability: Making sure only approved users can access information and systems when they need to.
Why Are IT Audit Controls Checklist Important?
IT audit controls are very important for a few key reasons. Let’s closely look at some of these reasons:
- It reduces the risk of hackers getting into your systems and stealing sensitive data. With strong controls, it is much harder for hackers to break into your system.
- It helps you follow rules and laws for your industry. Many businesses must have certain security controls in place to stay compliant with regulations.
- It keeps your data safe and secure. Good controls lower the chances of data breaches or leaks that could expose sensitive company information.
- It keeps your systems running smoothly. Clear IT controls make sure your IT can keep working properly, even during issues or outages. This prevents costly downtime and prevents your business from going into a loss.
What Are The IT Audit Controls Checklist?
In this section, let’s talk about key things to look at when checking the safety of your tech systems:
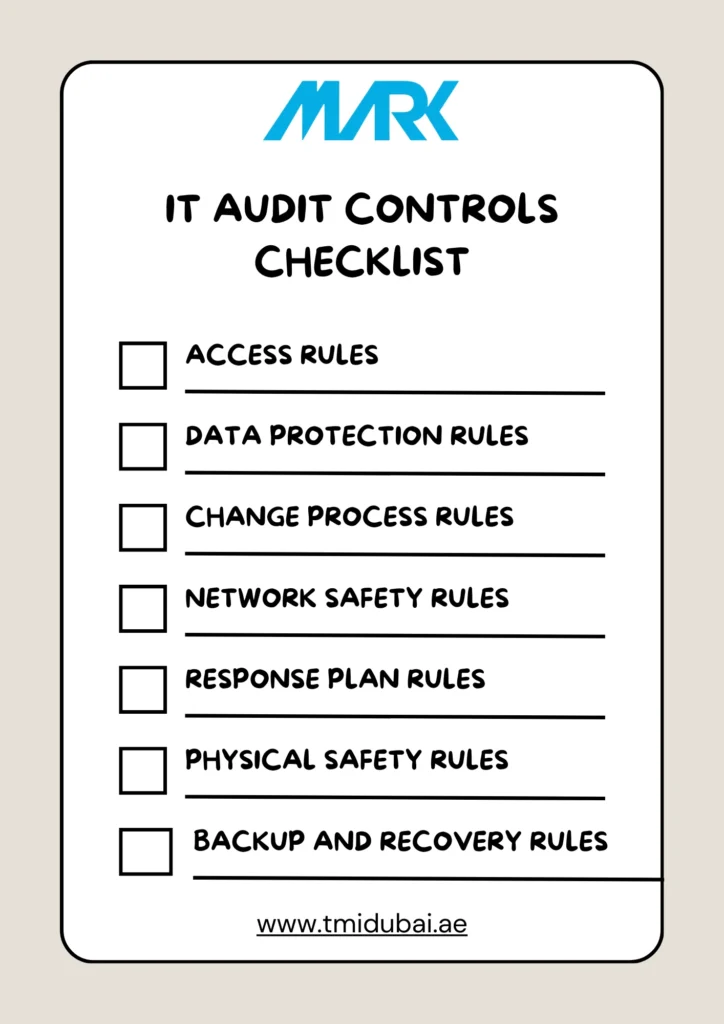
| IT Audit Controls Checklist | Description |
| Access Rules | Make sure the right people can get to your systems and data. Use hard-to-guess passwords and two-step logins. Check who has access often to keep things safe. Passwords like “yourname123”, “nameDOB123” are easy. |
| Data Protection Rules | Your data should be secure when it is stored or moving around. You can do this by scrambling data, so nobody can read it without special codes. |
| Change Process Rules | Have a straightforward plan for approving and safely updating IT systems. IT systems need to change over time to keep up with new tech. |
| Network Safety Rules | To prevent hackers from exploiting your system, use firewalls. |
| Response Plan Rules | The plan should focus on spotting, limiting, and fixing the problems. |
| Physical Safety Rules | Keep a track of physical access to server rooms |
| Backup and Recovery Rules | Backup the data regularly and keep a disaster recovery plan ready. |
IT Audit Control
- Access Rules: Decide who can use what systems and data. Use strong passwords, two-step logins, and check who has access often to your tech systems.
- Data Protection Rules: Scramble data when stored or sent. Have rules for what data is shared. Put a limit on who sees your sensitive data.
- Change Process Rules: Have a clear way to approve and make safe changes to tech systems. This stops mistakes or security holes within your system.
- Network Safety Rules: Use firewalls, detection systems, and secure network settings to protect your network from hackers and intruders.
- Response Plan Rules: Make a plan to find, stop, and recover from security problems to limit any harm to your organisation.
- Physical Safety Rules: Secure access to server rooms and data centers where your tech gear is situated.
- Backup and Recovery Rules: Regularly copy your data. Have a recovery plan ready in case systems go down. This will help you prevent downtime and avoid unnecessary loss in your business.
How Can TMI Help You?
TMI Dubai gives you tech tools to keep your information secure. Our team can help in many ways:
- Check for risky tech issues: We find weak spots in your tech and show ways to fix them.
- Make rules for safe tech use: We make a plan, so everyone in your company uses tech safely.
- Check if tech safety rules work: We look at how well your current safety plans work and tell you how to improve upon that if required.
- Keep helping with tech safety: We guide you over time to make sure your tech stays secure in the long run
Frequently Asked Questions (FAQ’s)
Though in-house audits are helpful, getting an outside auditor is key. An outside auditor has a keen eye for any potential vulnerabilities and weaknesses. They can spot issues that those inside the company may miss. Outside auditors are experts at finding weak spots in processes and systems.
Each year, you should review your computer systems. This is known as an IT audit. However, you may need more audits. This depends on your business field and risks. If you make big changes to your systems, you should do another audit. This also largely depends on the type of IT audit control you follow within your organization.
You will get a report after an IT check. This report tells you what is good and what is bad with your tech safety. It will also tell you ways to make things better. TMI Dubai can help you fix any existing tech issues within your company. Your tech safety will get better if you do the steps mentioned by our IT experts in the audit report.
Regular checks on your tech are super important. The price can differ based on how much needs to be looked at. But the cost of a data leak is way higher than an IT audit. Getting tech audits often is a wise way to avoid big problems in the future. Please remember, a small cost for safety is always better than a massive bill from a data breach.
All employees must learn about safe IT habits within your organization. This training helps them know the right way to act in certain situations. They also learn why safety rules are needed within the organization. These IT rules helps them to protect the company’s sensitive information at all costs.
Conclusion
IT rules help keep your computers safe. By following these rules, you can stop hackers from getting into your systems. You can also make sure you are doing what the law says. You can keep your sensitive information safe.
If you work with TMI for your IT control audit, you do not need to worry about anything. Your systems will be well-guarded and protected. We help you make smart choices about keeping your tech safe.
We stop any troubles before they become a big, and costly issue for your organization. Do not wait for the hackers to get in and mess up your systems. Call TMI now to talk about getting your IT checked.
Following IT rules helps to build a culture within the company where tech safety matters to everyone. TMI is the partner you can trust for strong IT safety. Let us lay a strong foundation today, so that your digital space can remain safe and secure in the future.