Your computer system is an important part of your business. You would want strong security to prevent break-ins and data theft A Vulnerability Assessment (VA) inspects for vulnerabilities.
A VA’s purpose is straightforward: identify computer system vulnerabilities, before hackers exploit them. It helps to solidify your defenses for increased security. In this article, we will explore what is the purpose of vulnerability assessment and more. Let’s get started.

Why is a Vulnerability Assessment Important?
Multiple websites store sensitive data like usernames and passwords. VAs safeguard these sites from hackers attempting information theft.
Let’s understand this with a real-life example. UAE has strict laws when it comes to data safety. For example, you own a company in Dubai. Your company website has employee and client data like name, address, banking details, etc. A hacker breach could lead to information misuse. VAs prevent such scenarios by detecting and addressing weaknesses before exploitation.
How Does a Vulnerability Assessment Work?
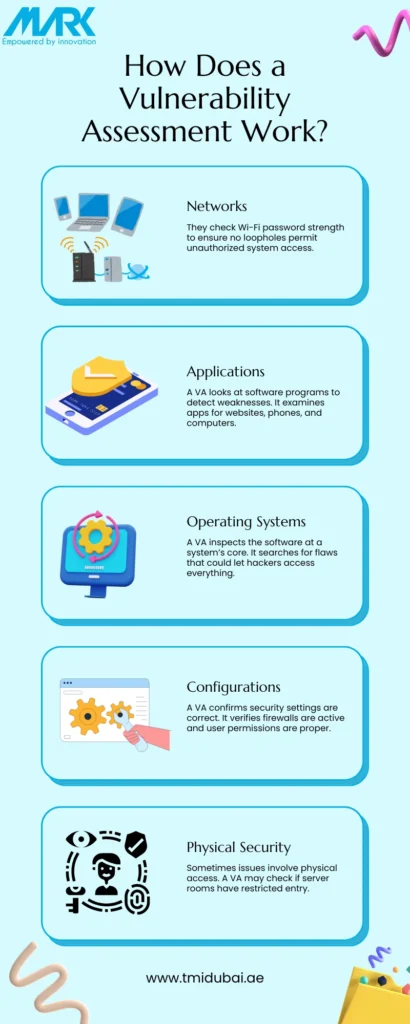
During a VA, our experts at TMI utilizes specialized tools scanning your system for vulnerabilities. They examine various areas:
- Networks: They check Wi-Fi password strength to ensure no loopholes permit unauthorized system access.
- Applications: A VA looks at software programs to detect weaknesses. It examines apps for websites, phones, and computers.
- Operating Systems: A VA inspects the software at a system’s core. It searches for flaws that could let hackers access everything.
- Configurations: A VA confirms security settings are correct. It verifies firewalls are active and user permissions are proper.
- Physical Security: Sometimes issues involve physical access. A VA may check if server rooms have restricted entry.
What Is a Vulnerability Assessment Report?
After examining your system, a report gets made. This vulnerability assessment report includes:
- Identified Vulnerabilities: It lists each problem found, rating severity from critical (major threat) to minor (minimal risk).
- Potential Impact: It explains how serious each issue could be including critical flaws, risks, data breaches etc. Less severe flaws allow limited unauthorized access.
What Doesn’t a Vulnerability Assessment Cover?
A vulnerability assessment identifies potential weaknesses in a system. However, it has limitations.
- New security flaws (zero-day attacks) remain undetected until discovered. While a VA cannot spot them, it improves the system’s defenses against such threats.
- Hackers may deceive people into sharing sensitive data (social engineering). Though VAs do not address this directly, they raise awareness about these tactics.
What Are The Benefits of a Virtual Assessment?
Conducting a VA increases your digital security, providing numerous advantages:
- Prevents data breaches: It uncovers vulnerabilities before exploitation. This leads to the prevention of data breaches.
- Improves system security: If you resolve identified weaknesses, it improves your system against cyber attacks.
- Boosts trust: Systems that are validated through VAs leads to user confidence in using the system and their information protection.
- Reduces compliance risks: A VA helps ensure compliance with industry data. It helps to eliminate the potential risks.
What Are The Different Types of Vulnerability Assessment?
Different types of VAs exist to meet different organizational needs. They include various methods:
- Web apps, for online shopping or games, get Web VA checks. It looks for hacker paths to steal user data.
- With mobile apps booming, Mobile VA is key. It assesses app security risks that could violate privacy or give improper access.
- Network VA dives deep into firewalls, routers, and network hardware. This ensures secure systems and blocks outside access.
- With businesses moving operations to the cloud, Cloud VA assesses the security of that environment. It includes storage, access control, and data encryption.
- Internal VA mimics attacks from unhappy insiders exploiting weaknesses within the company.
- External VA simulates hacker assaults from the outside. This helps to find vulnerabilities they could exploit to breach systems.
How To Choose The Right VA for Your Needs?
Which VA service you need depends on several things. This includes:
- The extent and intricacy of your framework matter: Large setups with many apps and an intricate network infrastructure could demand an extensive VA over simpler organizations in the UAE.
- Regulations in your field: Certain industries face specific data security rules. A VA can help verify your system and follow the compliance rules.
- Risk acceptance levels: Major firms in UAE handling sensitive information like financial details or health records might require rigorous VA approaches.
How To Prepare for a Vulnerability Assessment?
Before a VA, prep is key. Here is what you can do:
- Define the scope: Clearly outline systems and apps included in the VA.
- Establish objectives: Decide what you want from the VA – whether you want to find critical flaws or ensure adherence to regulations.
- Gather information: Provide VA crew with required system information like network diagrams, software versions, and security policies.
How To Follow Up After a Vulnerability Assessment Report?
A VA report is useful but this is just the first steps. Next steps include:
- Prioritize vulnerabilities: Tackle the most vulnerable outcome first. As those exploited could have severe impacts on your organization.
- Craft remediation strategy: Make a plan to fix flaws, and allocate resources and timelines for tasks.
- Implement remediation and check: To fix the weak spots, you need to take action. Then, make sure to check if your work has been effective.
- Do more tests: Consider repeating assessments once you have applied fixes. Check if the issues are handled correctly.
How To Create a Long-Lasting Culture of Security Within Your Organization?
VAs are invaluable, yet cybersecurity needs ongoing effort. Here is how to cultivate a lasting security-minded culture:
- Assess risks regularly: Don’t wait for the next VA. Identify and address potential weaknesses through periodic risk assessments. You can take the help of our experts at TMI Dubai for regular risk assessment.
- Train staff on security: Employees are often the systems’ weakest links. Educate your team about cyber threats and secure online practices with the help of our trained IT staff.
- Keep monitoring continuously: Threats can evolve without stopping. Use security tools that constantly monitor for suspicious activity and vulnerabilities.
- Stay updated on threats: The cyber landscape shifts rapidly and can lead to the emergence of new cyber threats. To stay safe, subscribe to our security blogs, follow our experts, and attend conferences to stay informed with the latest trends and security updates in UAE.
Frequently Asked Questions
Though focusing on security holes, a VA might expose underlying performance issues. However, it is not a replacement for optimization tools.
Even without sensitive information stored, a VA can be useful. Hackers might exploit your system to launch attacks on others or steal login credentials for your various online accounts. A VA helps identify weaknesses they could exploit.
The frequency depends on your specific risks and tolerance. However, it is advisable to do VAs regularly, at a minimum once yearly. Some organizations opt for quarterly VAs due to constantly evolving threats.
Free and paid VA tools exist online. But these tools might be limited and not as thorough as a VA done by a security pro. Experts have the skills and experience to interpret results and recommend suitable remediation.
VA costs vary based on your system’s size, complexity, and assessment scope. Options exist for different budgets. Start with a basic VA targeting critical vulnerabilities and explore more comprehensive assessments as your personal and organizational needs evolve.
Conclusion
Following the steps mentioned in this article and collaborating with our experts at TMI Dubai can significantly reduce vulnerabilities and build solid defenses against cyber threats.
A VA is a valuable tool. But it is just one part of the puzzle. You need to cultivate a security culture and prioritize vulnerability reduction. It can transform your digital infrastructure and protect your information and systems from a potential breach.








